- Solutions
- / Twilight Cyber
Cyber-intelligence solution for credentials
Twilight Cyber
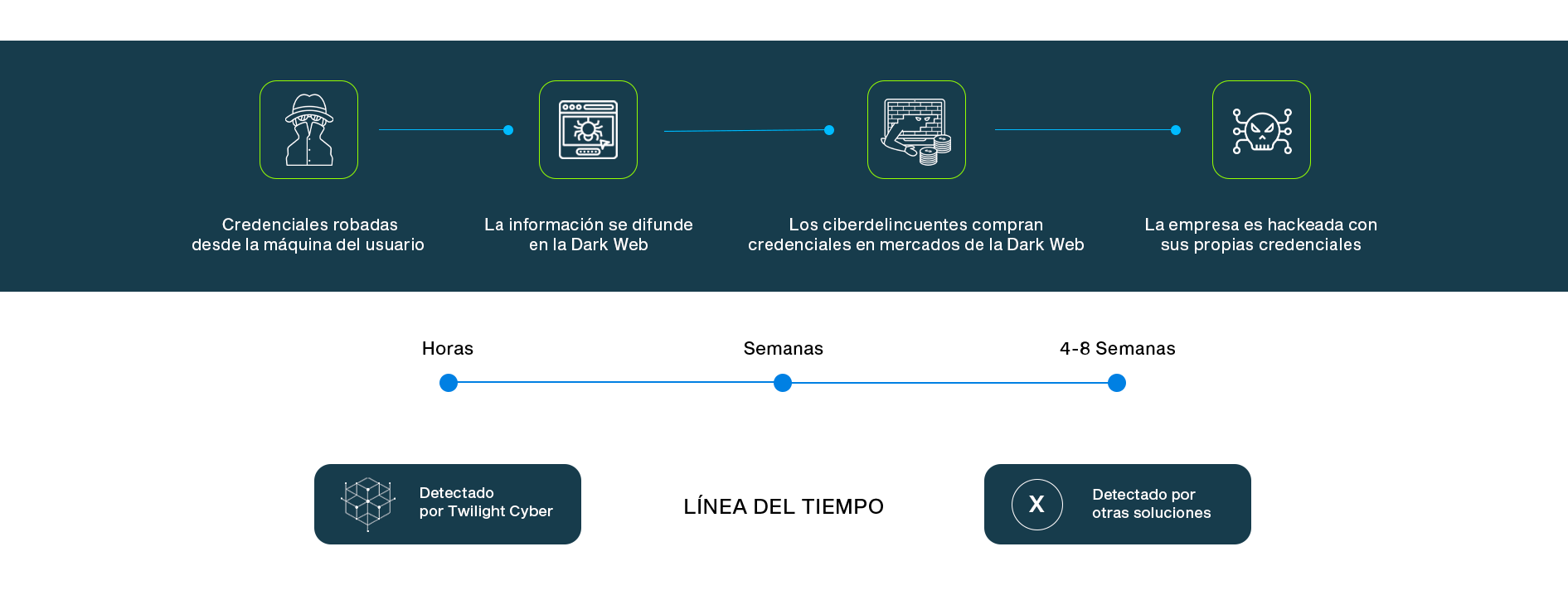
It detects in real time if your employees' and clients' credentials have been compromised on the Dark Web, unlike other technologies that take 4 to 8 weeks to do so.
Compromised devices
Infected machines every month.
Exposed access
Leaked credentials detected per month.
Efficiency
Reduction in the time spent on forensic analysis of breaches.
Twilight Cyber
-
Twilight Cyber offers advanced real-time detection of breaches in machines and credential leaks, monitoring the dark web to identify risks within hours of the incident.
This enables immediate action, neutralizing the use of compromised credentials and protecting the company's assets before they can be exploited in attacks such as ransomware or data breaches. It’s a key capability that significantly enhances security and incident response compared to traditional solutions.

Detection - Twilight Cyber
Advantages for organizations
Prevents Unknown and Sophisticated Threats
Deceptive Bytes uses techniques similar to malware, creating a deceptive environment on the endpoint, making at least 98% of malware ineffective in attacking the system without prior identification.
Prevents Damage to Data and Assets
Ensures that no data or assets are lost or corrupted in the organization. Additionally, it operates in user mode, ensuring no downtime on the endpoint, even in the case of faulty patches.
Reduces Operational Burden
Easy to operate without the need for specialists, allowing security and IT teams to focus on other areas. Attack prevention reduces the time spent on incident investigation and system restoration, ensuring business continuity.
Reduces Reputational Risk
Protecting the integrity of companies involves preventing malware spread on endpoints, theft of confidential information, and data manipulation, avoiding impacts on reputation.


Advantages for CISO's & IT Managers
Automates Malware Response
Automatically neutralizes malware operations on the endpoint without the need for constant configuration or additional burden on the security or IT team, preventing attacks in seconds.
Adaptable to IT Environment Changes
Quickly adapts to changes in IT environments without the need to reconfigure or rebuild the entire implementation.
Reduces Alerts and False Positives
Provides accurate alerts that reduce security or IT team fatigue when handling other tools, decreasing the time spent on false alarms.
Operates in Unpatched and/or Vulnerable Environments
Since the solution creates deceptive information on the endpoint and modifies malware behavior in real-time, it frustrates attacks in unpatched or vulnerable environments.
Advantages for nivel-C
Improves Employee Productivity
Deceptive Bytes, being lightweight and consuming few resources, allows employees to work uninterrupted, unlike traditional tools like AV and EDR.
Reduces Operational Costs and Resources
By integrating with Windows Defender and Windows Firewall, the solution leverages built-in security tools without additional costs, eliminating the need for outdated and ineffective tools.
Protects Remote Employees
The solution protects employees working outside the organizational network without the need for constant updates, ensuring security even on connections from networks or devices that are not secure.


Advantages for MSP's & MSSP's
Enhances Client Resilience
By focusing on prevention rather than detection, you strengthen your clients' resilience, making malware attacks ineffective.
Manages Multiple Clients with a Single Server
This allows MSPs and MSSPs to save time, resources, and reduce operational burden.
Shifts from Threat Detection to Proactive Prevention
Using Deceptive Bytes, MSPs and MSSPs can shift their focus from detection to prevention, freeing up security teams' time to focus on client network security.
Focus on Other Client Threats/Risks
By providing an endpoint prevention solution, MSPs and MSSPs optimize time and resources, effectively addressing other threats faced by organizations.
Differentiators Twilight Cyber

Identification of leaks on the web, cloud, supply chain, and partner domains.

Machine Shutdown Compromised immediately, implementing additional security measures.

Real-time detection and alerts to take immediate action against leaks.

Continuous monitoring to identify security breaches and strengthen the security posture.

TWILIGHT CYBER | SOLUTIONS
One step ahead
-
Asset Protection
Detect compromised credentials instantly. Twilight's real-time dark web monitoring helps you prevent unauthorized access, data leaks, and financial losses.
If a machine is compromised, we notify you within hours so you can contain the threat immediately.

-
Account Takeover (ATO) Prevention
Secure credential authentication at every login and instantly detect compromised machines or credentials.
Its T-ATOP system updates information every hour, much faster than traditional platforms, allowing you to act before it becomes a problem.

-
Partner and Supply Chain Protection
A security breach in a supplier can jeopardize your business. Twilight Cyber identifies vulnerable credentials of your partners in real time, protecting your organization from supply chain risks.
-
OT Network and Critical Infrastructure Protection
Although OT networks are not connected to the outside, they can still be vulnerable. Twilight Cyber detects compromised credentials and machines with access in real time, maintaining the integrity of your infrastructure.